BioBundle is a medium reversing challenge on Hack The Box. The description is “We’ve obtained a sample of zombie DNA. Can you extract and decrypt their genetic code – we believe we can use it to create a cure…”
First we are going to run the file command on the binary to see what we got.
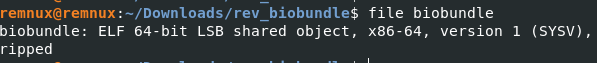
We have a lovely ELF binary. Let’s open it up in Binary Ninja and check the inner workings.
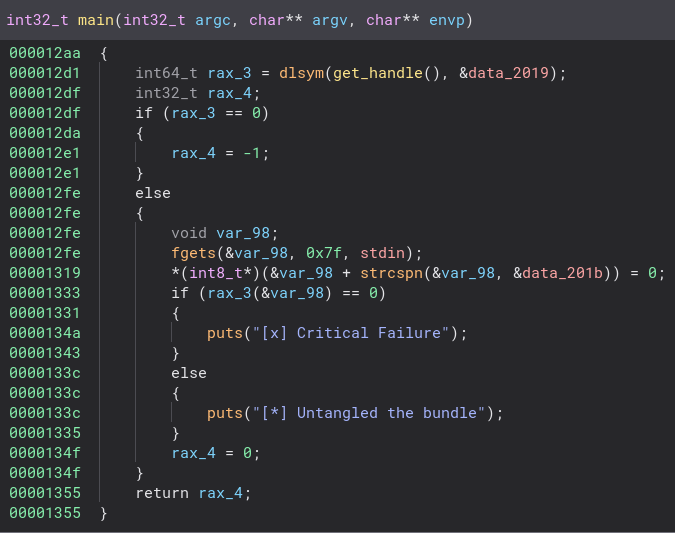
The main function looks pretty basic. Let’s check out the function “get_handle” and see if there is anything interesting in there.
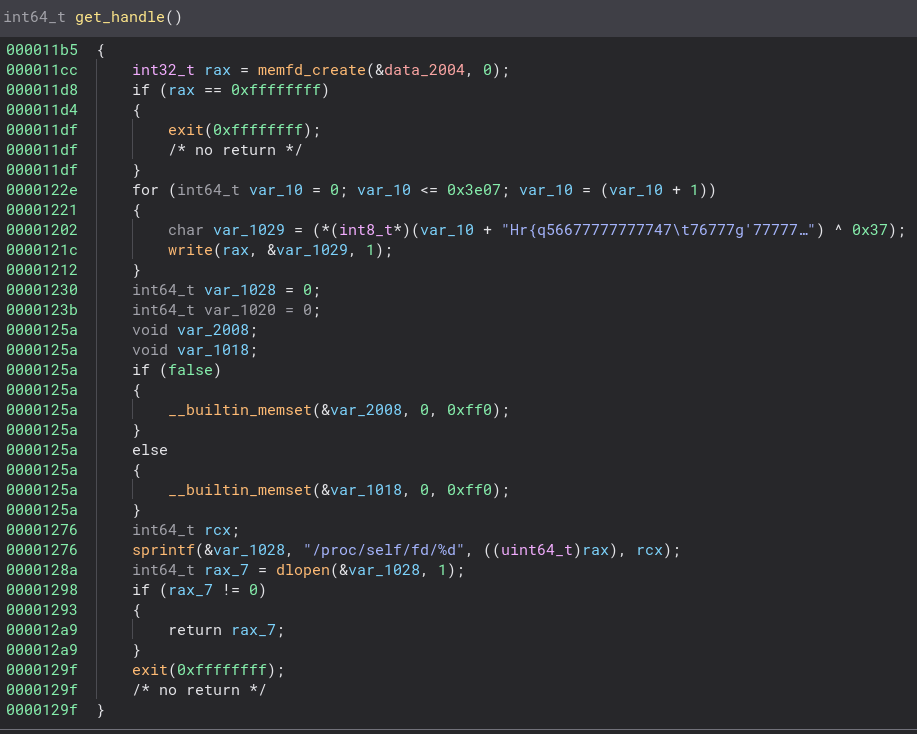
Now this is much more interesting for us. There are lots of interesting calls in this function such as “memfd_create” and “dlopen” There is also a VERY long XOR on some string. Let’s check the first few characters to see if we can get any hint of what that data is.
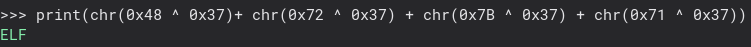
It looks like the first character is not valid ASCII, but the rest is quite telling! Looks like it is some kind of binary file. Now, let’s XOR all the data and write it to a file and see if that has more answers for us. Here is a python script I wrote to do just that.
elf = []
temp = ""
with open('biobundle', 'rb') as file:
fileData = file.read()
startOffset = fileData.index(b'\x48\x72\x7b\x71')
for i in range(startOffset, startOffset + 15879):
tmp = fileData[i] ^ 0x37
elf.append(tmp)
with open('biobundle2', 'wb') as file2:
file2.write(bytes(elf))
Running this script gives us a second binary. Let’s open that up in Binary Ninja.

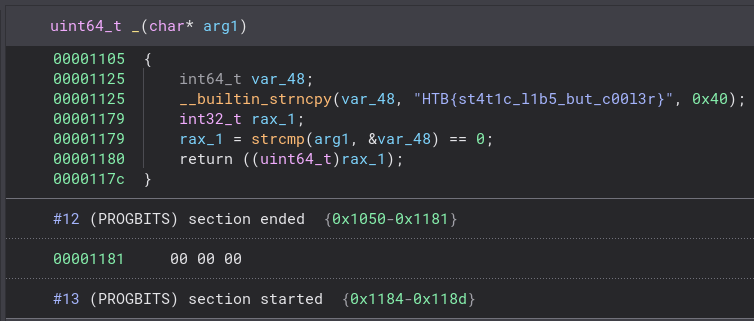
That looks like the flag! Let’s rerun the original binary with that as our input just to double check.
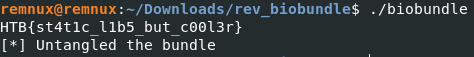
Looks like that is correct. The second binary looks a little odd and does not run, but it gives us what we need. I do not think this was the intended route to do this challenge, but it is definitely the easiest. I spent a lot of time trying to do it a different way by trying to read the file in memory, but I could not figure it out. I hope to come back to this challenge as I learn more and try it the intended way. Thanks for reading and happy reversing!

Leave a comment