Rebuilding is a easy reversing challenge on Hack The Box. The description is “You arrive on a barren planet, searching for the hideout of a scientist involved in the Longhir resistance movement. You touch down at the mouth of a vast cavern, your sensors picking up strange noises far below. All around you, ancient machinery whirrs and spins as strange sigils appear and change on the walls. You can tell that this machine has been running since long before you arrived, and will continue long after you’re gone. Can you hope to understand its workings?”
First, let’s run the file command to see what kind of binary this is using the command file rebuilding
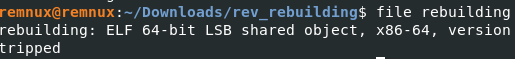
We got a nice ELF binary. Next, let’s open it up in Binary Ninja and check out the inner workings.

This is just a small snippet of the main function. The first things I notice are the check for password length and the nested for statements. Scrolling down we see what appears to be the code that gives us the flag. I am going to rename a few variables to make it easier to read.

It looks like there is some division which looks off in my version of Binary Ninja, but we can infer that it is the length of the key for XOR purposes. Here is that line of code rewritten to be a bit easier to read.
checkedVariable += encrypted[i] ^ key[i % 6] == input[i];
This code checks character by character if “encrypted” XORD by “key” equals our input. If it does it adds one to checkedVariable, if not it adds zero. If all the characters in our password equal “encrypted” XORD by “key” then we have the password and it puts out the password is correct message. Now let’s find these two variables “encrypted” and “key” so we can make a script to decrypt them.
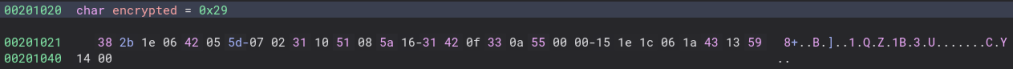
Encrypted is easy to find as it is just in the data section.
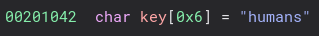
Next, we need to find the key. We need to change the typing to char and then we can see the key in the data section.
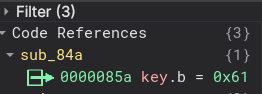
If you were to try this though, it would not give you the correct output, because that is not the right key. If you click on the key and look at the cross references, you can see it is actually changed in the code.

Now that we have the actual key, we can make our python script to decrypt the password.
encrypted = b'\x29\x38\x2b\x1e\x06\x42\x05\x5d\x07\x02\x31\x10\x51\x08\x5a\x16\x31\x42\x0f\x33\x0a\x55\x00\x00\x15\x1e\x1c\x06\x1a\x43\x13\x59\x14'
encryptedList = list(encrypted)
key = b'aliens'
flag = []
for i in range(len(encryptedList)):
temp = encryptedList[i] ^ key[i % 6]
flag.append(chr(temp))
print(''.join(flag))
Running this script will give us the flag!

This challenge stumped me for a bit with the whole changing key thing, but once I really looked through the code it was easy to figure out. Thanks for reading and happy reversing!

Leave a comment