FlagCasino is a very easy reversing challenge on Hack The Box. The description is “The team stumbles into a long-abandoned casino. As you enter, the lights and music whir to life, and a staff of robots begin moving around and offering games, while skeletons of prewar patrons are slumped at slot machines. A robotic dealer waves you over and promises great wealth if you can win – can you beat the house and gather funds for the mission?”
First, we are going to run the file command on the executable. We get a lovely 64-bit ELF binary.
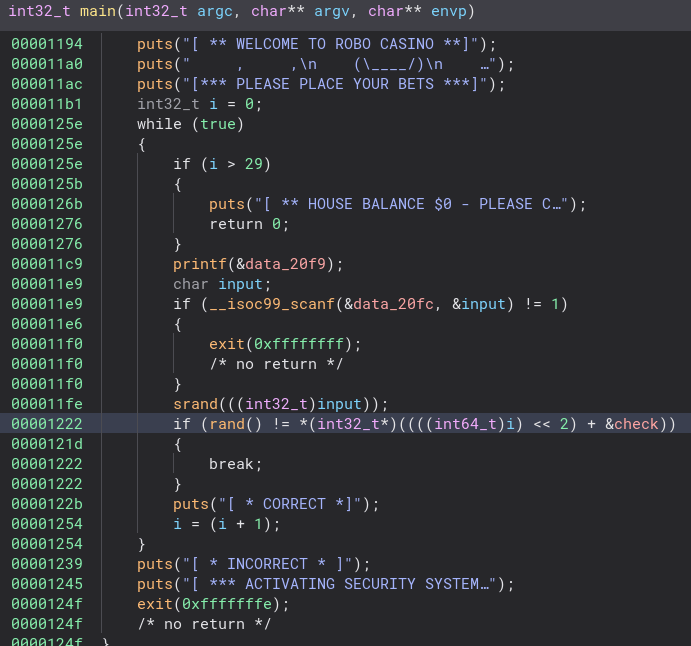
Next, let’s open it up in Binary Ninja. I went ahead and changed a few variable names and data types to make it easier to read, but the code is pretty simple. The program prints a few lines, gets our input, uses it as a seed, gets a random number from that seed, and finally compares that against a list of numbers. You may also notice in the comparison the program bit shifts i left twice and then adds that to the number in the variable, but I think that is de-compiled wrong. Later when we get to programming the solution, if you add a “i << 2”, you will not get the correct solution. You will only get it right if you bit shift by 0, which is the same as doing nothing, so we will skip it in our solution. If you know why this is, please let me know.
Now that we know what the program does, we need to find a way to crack it. Let’s take a look at the numbers in the check variable.
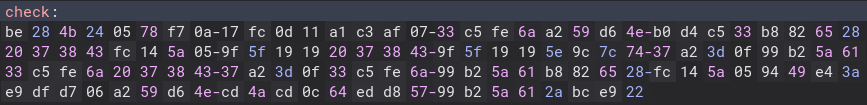
We know there are 30 characters because of the i loop stopping at 30 and there are 120 bytes of information, so each check is against 4 bytes. Now, we can split the string up into sections of 4 bytes. To do that I used a simple python script. We also need to change the bytes into little endian format, so we will have the script do that for us as well. Here is that script.
from textwrap import wrap
a = "be284b240578f70a17fc0d11a1c3af0733c5fe6aa259d64eb0d4c533b882652820373843fc145a059f5f1919203738439f5f19195e9c7c7437a23d0f99b25a6133c5fe6a2037384337a23d0f33c5fe6a99b25a61b8826528fc145a059449e43ae9dfd706a259d64ecd4acd0c64edd85799b25a612abce922"
b = wrap(a, 8)
c= []
for i in range(len(b)):
d = b[i][6]+b[i][7]+b[i][4]+b[i][5]+b[i][2]+b[i][3]+b[i][0]+b[i][1]
c.append(d)
print(c)
It is not pretty, but it gives us what we need. Here is part of the output.
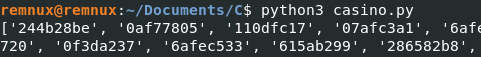
Now that we have a list of these hex numbers, we can do a bit of search and replace to make it a valid C array. Next, we can remake the program and add some brute forcing to give us the correct flag. Here is my C program.
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main() {
int a[] = {0x244b28be, 0x0af77805, 0x110dfc17, 0x07afc3a1, 0x6afec533, 0x4ed659a2, 0x33c5d4b0, 0x286582b8, 0x43383720, 0x055a14fc, 0x19195f9f, 0x43383720, 0x19195f9f, 0x747c9c5e, 0x0f3da237, 0x615ab299, 0x6afec533, 0x43383720, 0x0f3da237, 0x6afec533, 0x615ab299, 0x286582b8, 0x055a14fc, 0x3ae44994, 0x06d7dfe9, 0x4ed659a2, 0x0ccd4acd, 0x57d8ed64, 0x615ab299, 0x22e9bc2a};
for (int i = 0; i < 30; i++) {
for (int j = 33; j < 126; j++) {
srand(j);
if (rand() == a[i]) {
printf("%c", j);
}
}
}
printf("\n");
return 0;
}
Once again it is not pretty, but it works. For anyone wondering why we test every number between 33 and 126, that is because those are the integer representatives of ASCII characters I thought could be in the flag. If we run this second program we will get the flag.
Now, we just have to enter the flag into the program and see if it is correct.
And there we go! We have completed the challenge. Thanks for reading and happy reversing!

Leave a comment