Tear Or Dear is an easy reversing challenge on Hack The Box. The description is “Find the username and password and put them in the flag in the format: HTB{username:password}
Warning: It can produce false positives.”
As always we are going to run the file command on the binary. Even though we know it is a Windows executable, we may learn other information that will help us reverse this binary.

Now we also know it is a .Net assembly. Let’s open it in dnSpy in Windows to see what we are working with.
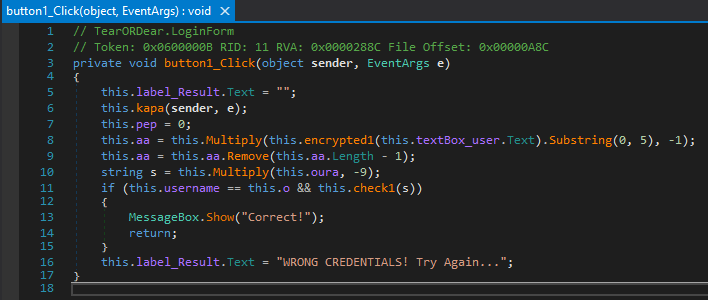
After looking through the functions the first one that pops out to me is the button1_Click function. This function is where the username and password checks are made. The first step is to figure out what “this.o” is. To do this we are going to set a breakpoint at the username and password comparison.
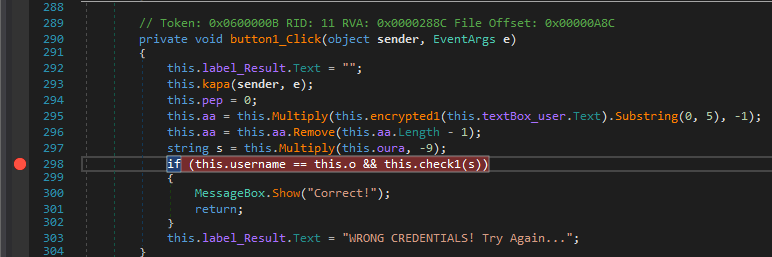
Now we are going to run the program to the breakpoint. This allows us to look at the variables the program is using. Now all we have to do is find “this.o”

Another thing I checked for what “this.username” I ran the program with “abc” as the username and “123” as the password, but “this.username” is 123. It seems the username and password fields are swapped.

Now we move onto the “check1” function that is called.
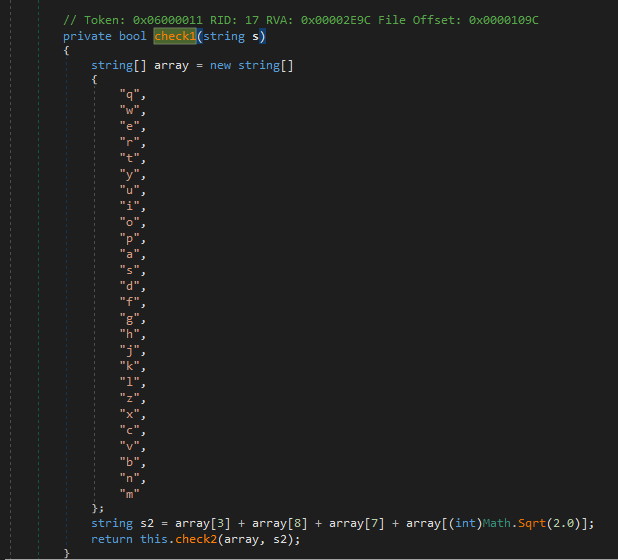
This function just makes a string and calls another function named “check2” This goes on a few times, but they do not really do anything we need to pay attention to. The important one is the last one just and it is just named “check”
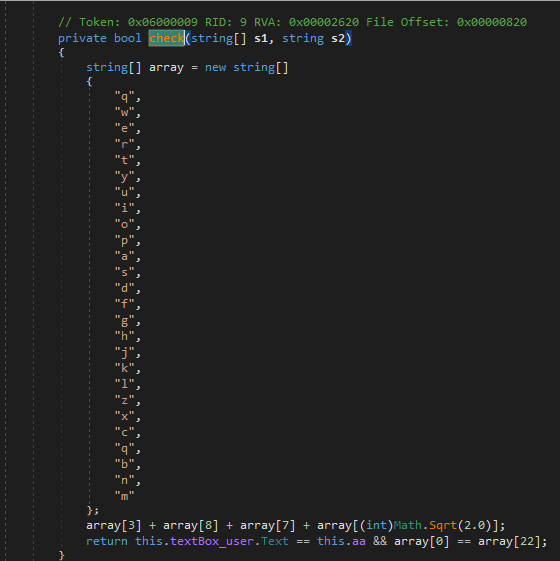
Now, the final local we need to look for is “this.aa”

If we combine all of this and make sure to remember that the username and password are swapped we get this!
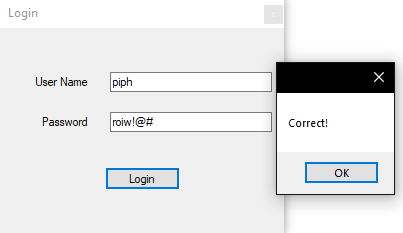
Challenges like this one make me wish everything was written in C# just for how easy they are to decompile. Thanks for reading and happy reversing!

Leave a comment