Secured Transfer is an easy reversing challenge on Hack The Box. The description is ” Ghosts have been sending messages to each other through the aether, but we can’t understand a word of it! Can you understand their riddles?”
First, we are going to run the file command to see what kinda file we are working with.
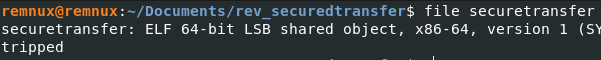
We have an ELF binary which means it runs on Linux. Also included with the executable was a Wireshark PCAP which we should keep in mind while reading the code.
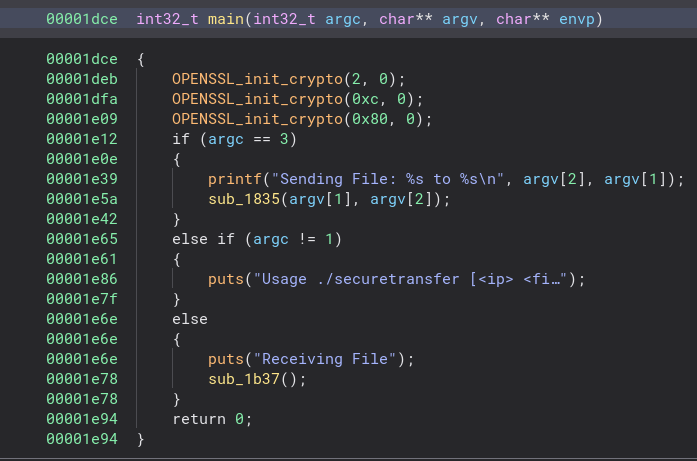
When opening the executable in Binary Ninja we are greeted with the main function. The first thing that sticks out to me is the OPENSSL crypto initialization and the “Sending File” string. Based off of this information and the name of the challenge it looks like this program encrypts files and then sends them. When using the program to send a file it calls the “sub_1835” function. This seems like a good place to start, so let’s get to it.
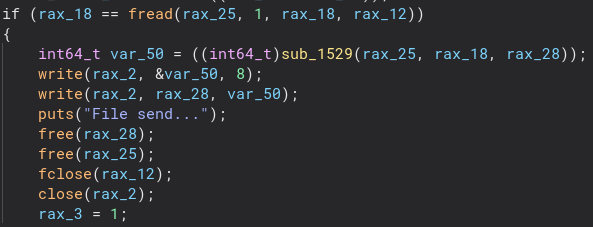
This function is pretty long, but most of it is error handling and file handling, so we can ignore most of it. This is the first section of code that sticks out to me since a function is called right before the file is sent. Now let’s check that function and see what we can learn.
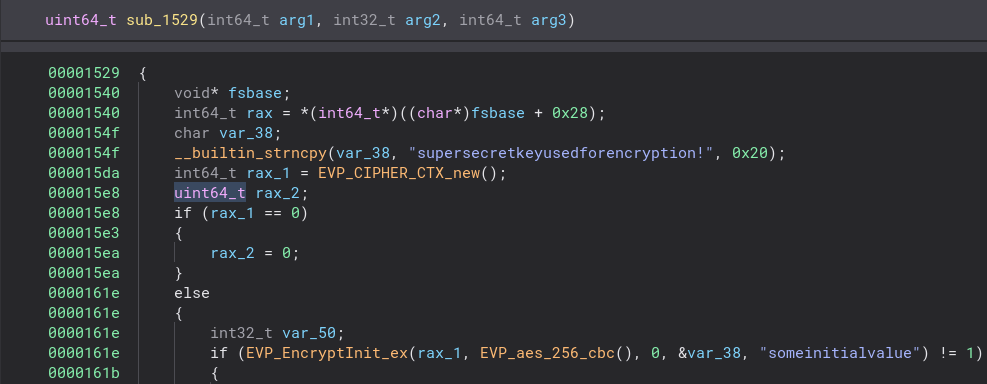
This is exactly what we are looking for. This is the encrypt function used to encrypt the files before sending them. Luckily for us they did not encrypt the encrypt function so everything we need is all in plain view. Now that we know how the file is encrypted, let’s check out the PCAP file and see what we can find.
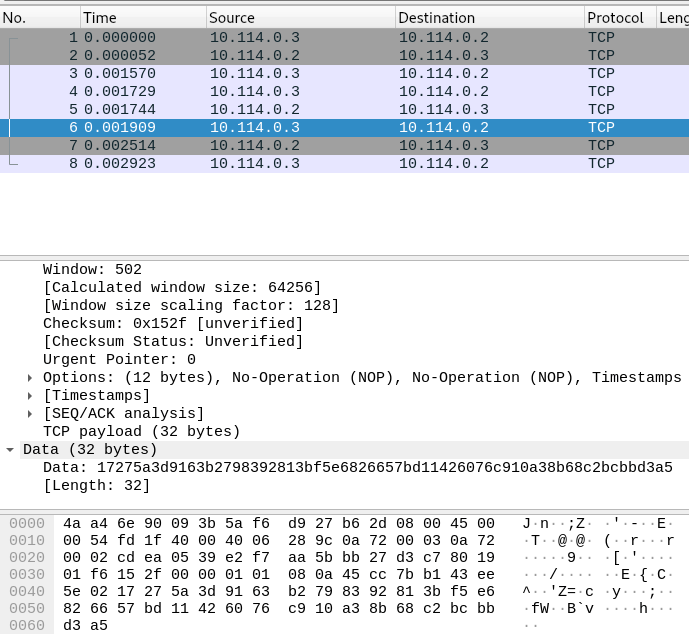
Checking through the packets sent we find one with some data in it. Let’s see if we can decrypt it using the info from the encrypt function.
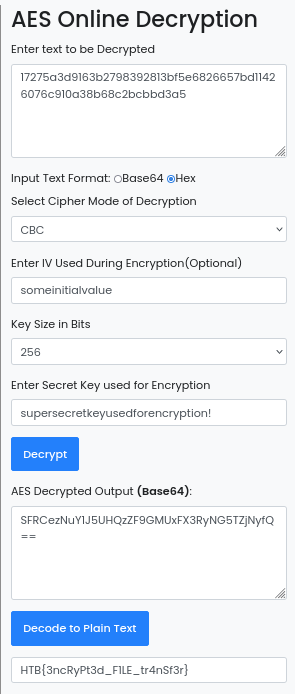
Plugging in all of the information in and we get the flag! Challenges with encryption always seem daunting to me, but this challenge was super easy as long as you did not get too caught up in the code. Thanks for reading and happy reversing!

Leave a comment