Hunting License is a very easy reversing challenge on Hack The Box. The description is “STOP! Adventurer, have you got an up to date relic hunting license? If you don’t, you’ll need to take the exam again before you’ll be allowed passage into the spacelanes!”
The first thing we are going to do is run the file command on the file to see what we are working with.

It is an ELF binary which means we can run it on our current system. Next, we are going to go ahead and give it a run to get a sense of what the program does.
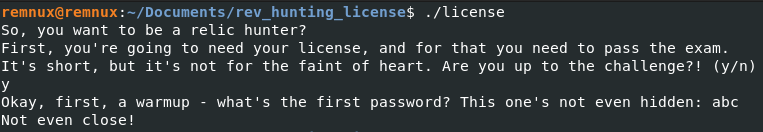
It prints some text and asks if we are ready. After saying yes, we are asked for a password. Unfortunately our first guess was incorrect. Now let’s open it it in Binary Ninja and see how the program works.
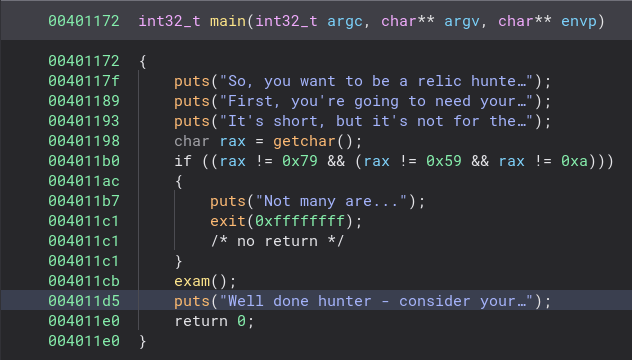
Looking at the main function we can see where it prints the text and where it checks if you are ready for the test or not. Then it runs a function named exam. That seems like the next logical place so let’s go check that function out.
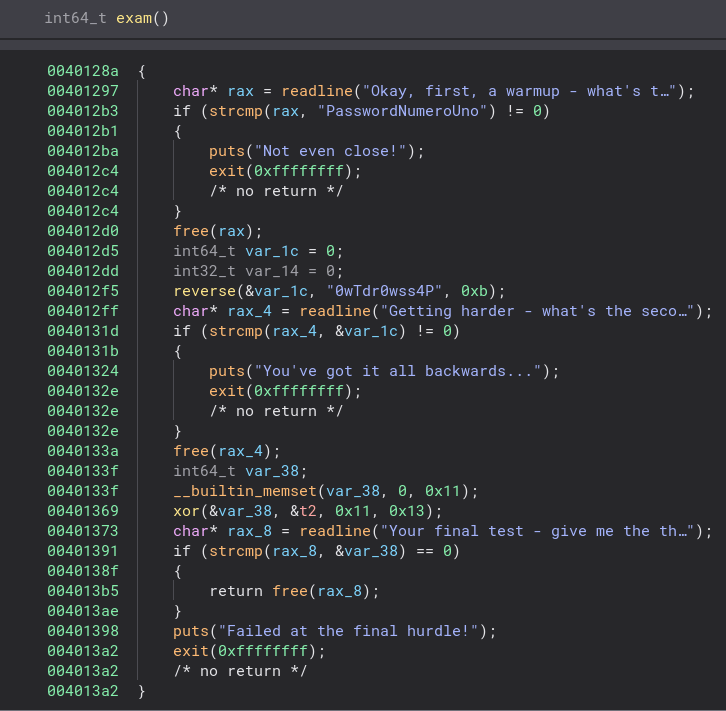
This function is where all of the password checks are at. The first one is very simple and compares your input with “PasswordNumeroUno“. Checking this with the program, we see it is correct.

Now for the next password.
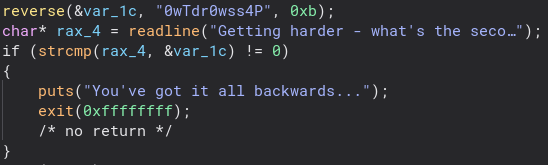
This one is slightly more complicated. A function named reverse is called on a string and then that is compared with our input. Without checking that function we can assume the name is what it does to the string and give “P4ssw0rdTw0” a try.
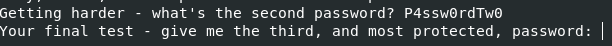
It worked! Now for the third password.

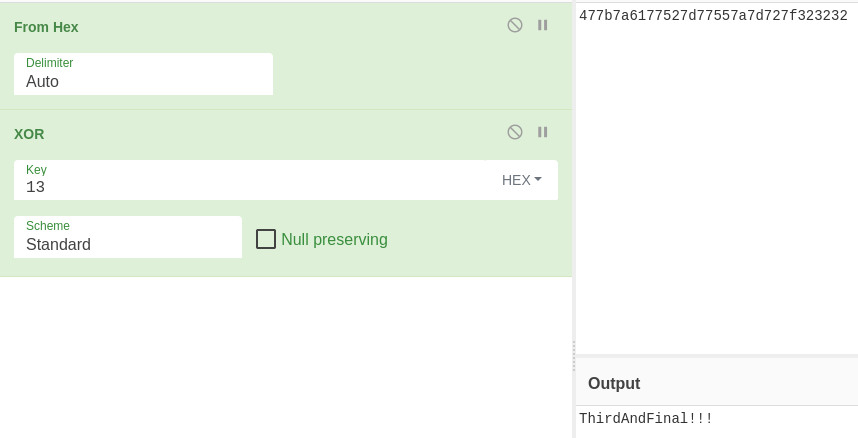
Once again it gets slightly more complicated. This time instead of reversing a string, it is XORing it instead. Going to &t2 we can see the string that is XORd.

Copying these hex bytes and XORing them by 0x13 gets us the third and final password.
Now let’s give that a test.

Now let’s connect to the IP given to us by Hack the Box and see if there is anything else we need to do.
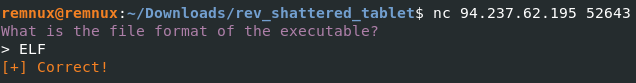

There are more questions to answer! The first two answers are easily answered from the file command we ran earlier.
The next two are easily answered from our decompilation from earlier.
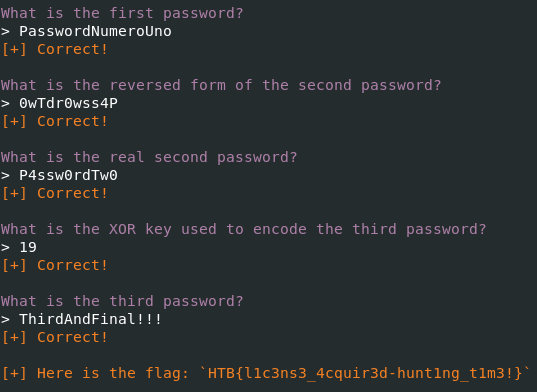
The last few questions are about the passwords and how we got them. And like that we are done! That is a fun and simple challenge to get started in reverse engineering. It also gives you a glimpse into some common obfuscation methods such as xor which are used in quite a few challenges. Thanks for reading and happy reversing!

Leave a comment