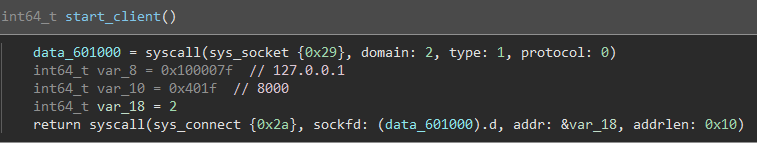
IRCWare is another easy reversing challenge on Hack The Box, but do not let the difficulty fool you it is no where near as easy as the last challenges. The description is “During a routine check on our servers we found this suspicious binary, although when analyzing it we couldn’t get it to do anything. We assume it’s dead malware, but maybe something interesting can still be extracted from it?” Running the program seemingly does nothing so off to Binary Ninja we go. There are quite a few functions and syscalls in this program so I begin to examine and rename them. The main function does not seem to really do anything interesting itself, but it does call another function which I renamed to start_client. We will now take a look at that function.
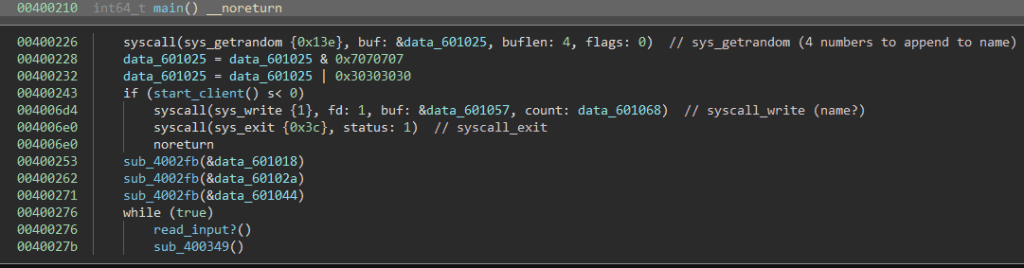
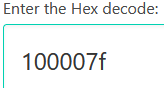
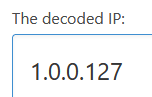
The start_client function is where things start to get interesting. First, the program opens a socket and then it uses that socket and opens a connection to it on 127.0.0.1:8000. These numbers took me a while to figure out due to endianness.
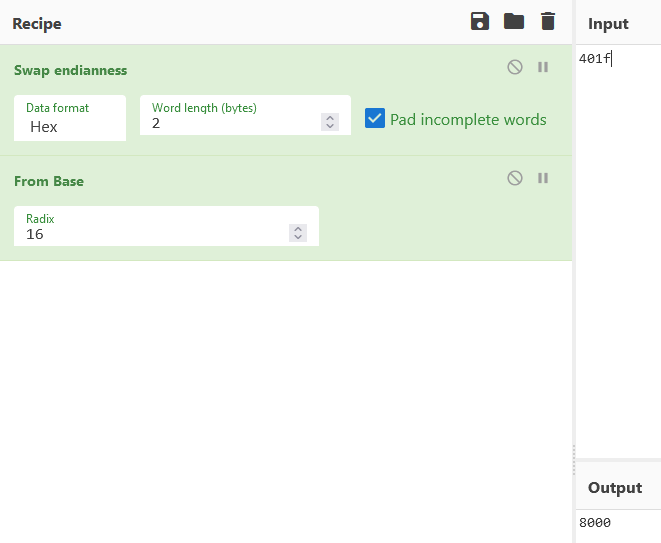
Now that we know at least some of the functionality let’s try and run the program with a listener setup. While looking through the strings I found some interesting ones so lets give them a try. I attempt to run the flag command and it says it requires a password. Now to figure out how to get that.
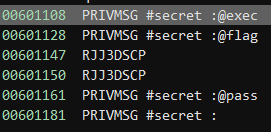
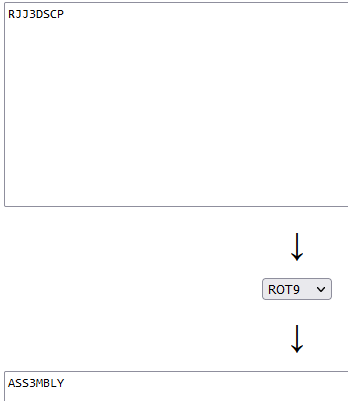
Another interesting string I found was “RJJ3DSCP.” After going to where it is referenced I find this block of code. As you can see from my comments it seems this function checks the characters one by one of your input against the ROT9 of “RJJ3DSCP.” This was slightly confusing since it first adds 17 then subtracts 90 then adds back 64 which gets you to -9.

Putting that string through ROT9 we get “ASS3MBLY.” This seems to be the correct password so let’s give it a try.
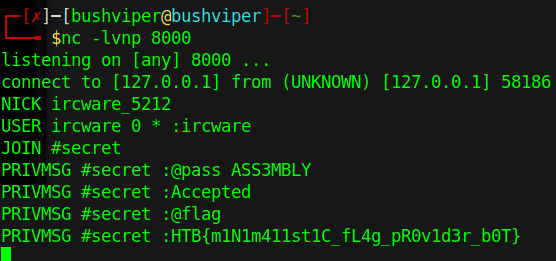
The password is accepted and we now have the flag. This challenge took me a long time to figure out even though it does not seem so complicated when looking back. Just trying to figure out what IP and port the program connects to took me a long time. Thanks endianness! Even trying to run the commands took a while since I did not think you had to type the whole thing. This challenge taught me a lot and was a lot more in-depth than the other ones I have done so far. Thanks for reading and happy reversing!

Leave a comment