This is going to be our last super easy reversing challenge from Hack The Box for a while as we begin to go further in difficulty. The description of this challenge is “Show us your basic skills! (P.S. There are 4 ways to solve this, are you willing to try them all?)” We first run the program to see what we are dealing with. It is another classic “password” type challenge. Once again they did not select “aaa” as the password so off to Binary Ninja we go.
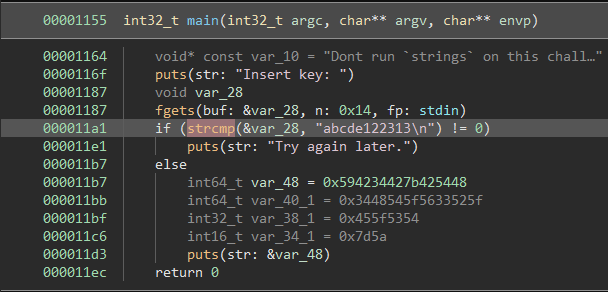
Immediately we see in the main function there is a “strcmp” with what looks like the password. You could also decode the four hex strings and reverse them to get the flag if the password wasn’t as easy to find.
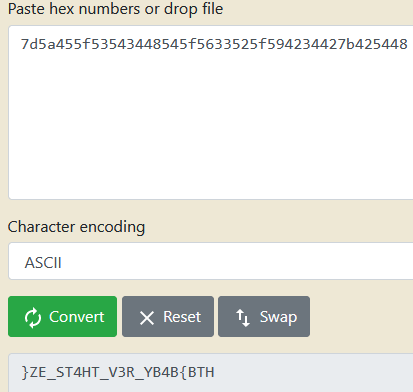
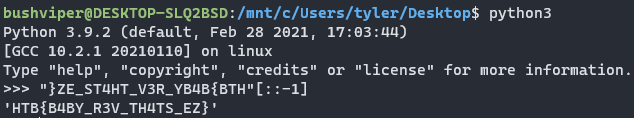
Using that string as the input we get the flag.
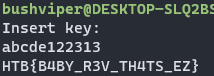
Since this challenge is so easy we are going to go over all four (and maybe five) ways of completing it. The next way is with “ltrace”. Running the program through “ltrace” and then putting any random input also gets you the correct password.
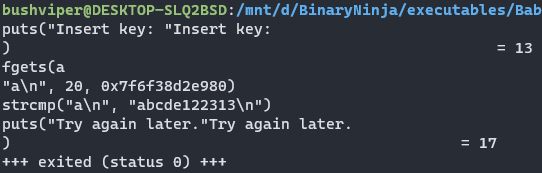
The third way is also through dynamic analysis, but we will be using a debugger instead. I first open the program with” gdb + pwndbg”. I start by disassembling the main function so I can find where to set a breakpoint.
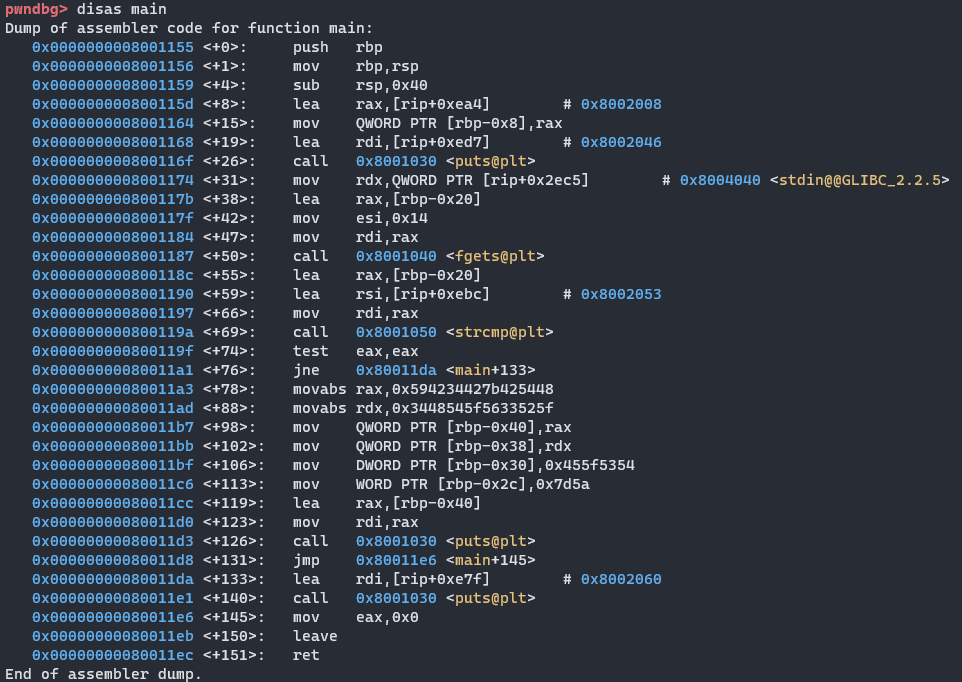
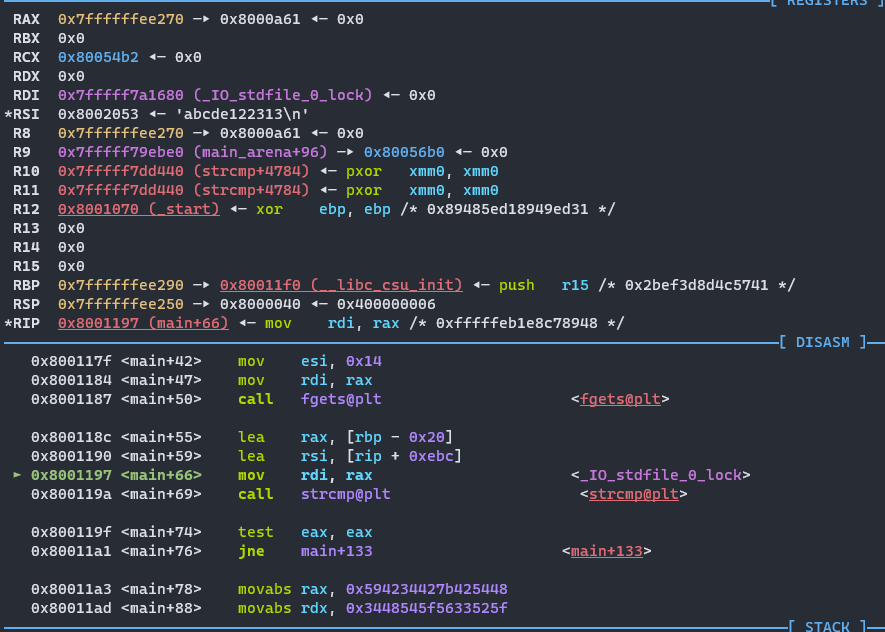
I decide to break at 0x8001190 since that is where the correct password is loaded which we can see by our static analysis of the program. I then start the program.
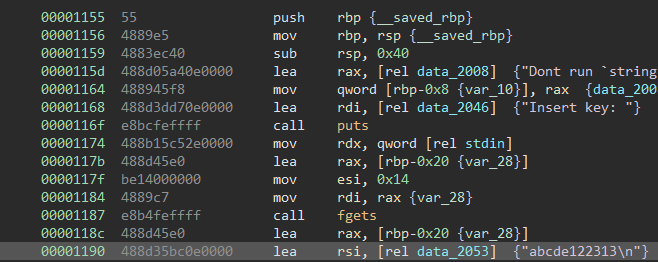

After we start the program we are thrown straight into the main function. Here we use the “continue” command to go to our breakpoint. We once again put in random input as it does not matter.
We are now at our breakpoint, but our password is still not loaded. We do a quick “step” and our password is loaded into “RSI”.
The fourth and final way we are going to solve this challenge is though some good old binary patching which would be extremely useful if we could not find the correct password easily. We open the program back in Binary Ninja and go to the main function. The code works by comparing our input with “abcde122313”. If the inputs are NOT equal it jumps to the unsuccessful message. If we “NOP” this “JNE” then we will run the successful message regardless of our input.
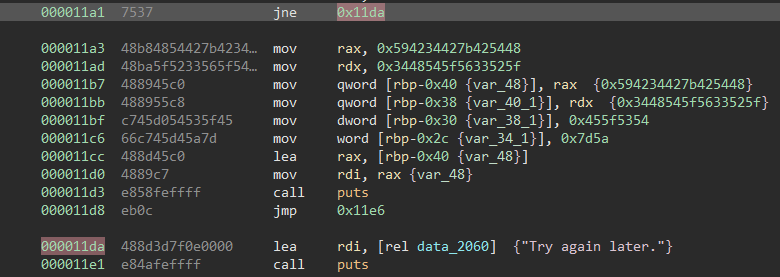
We rightclick the “JNE” line and select edit current line.
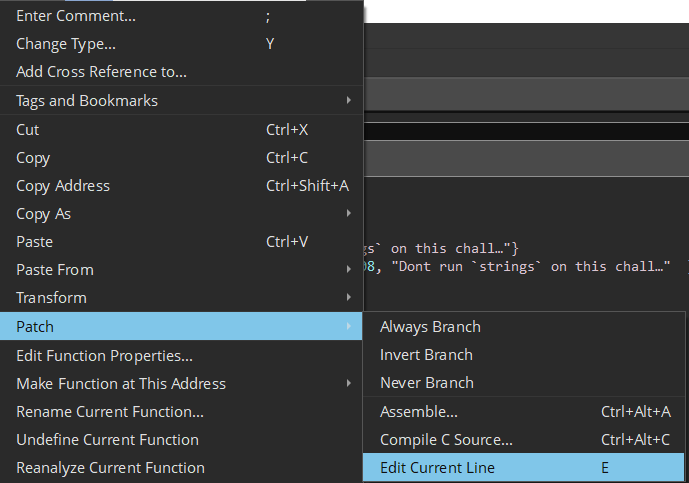
We then “NOP” the instruction and save the program.


Now it is time to test our patch. We run the program and give the wrong input, but we still get the flag back.
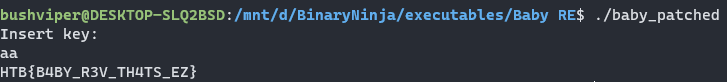
And there are four ways to complete the Baby RE challenge. This challenge is good practice and I highly recommend completing it as many ways as you can. Thanks for reading and happy reversing!
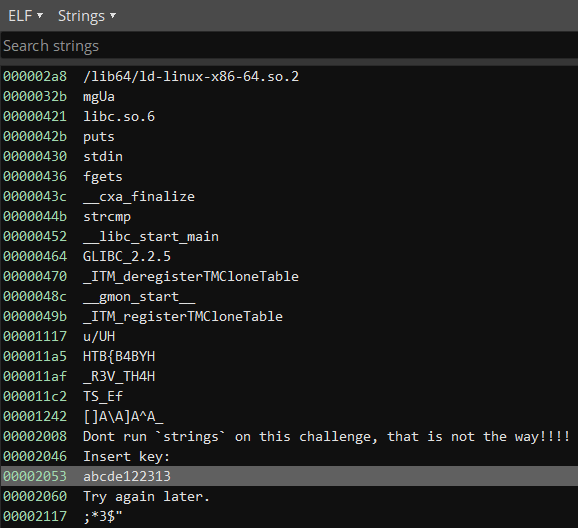
And for a secret fifth way you can run strings on the challenge just like they tell you not to 🙂

Leave a comment