Anti Flag is an easy reversing challenge on Hack The Box. The description is “Flag? What’s a flag?” This one has some fun anti-debugger/ltrace elements in it. I first run the program with nothing attached to it and I get this back.
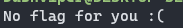
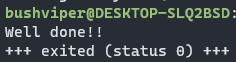
Running it with “ltrace” gives me a different response. Let’s open this up in Binary Ninja.
The main function seems pretty simple in this program with one very noticeable quirk, PTRACE. This seems to detect if a debugger is attached to the program. Another interesting thing is there are quite a few lines of code missing from the de-compilation.
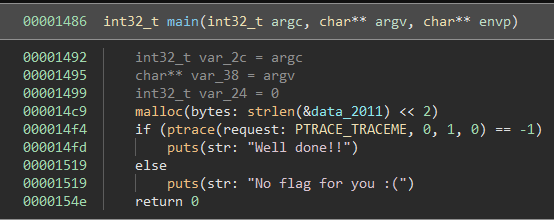
Looking at these lines in the disassembly view we can see them. There is an interesting string and also an interesting call to a function. Let’s try and access these lines of code with some binary patching.
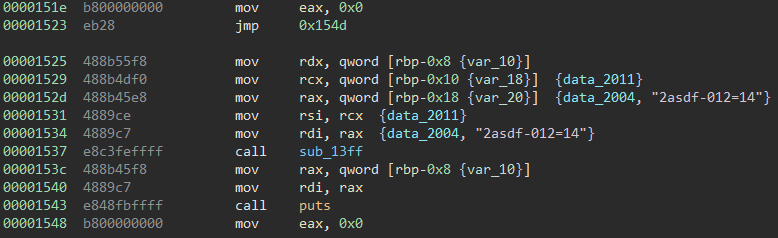
We are going to repurpose this “JNE” to take us to the unreachable code. Instead of “NOP”ing it, we are gonna instead turn it into a “JMP 0x1525” It seems to change the code quite a bit, but we are not worried about that.
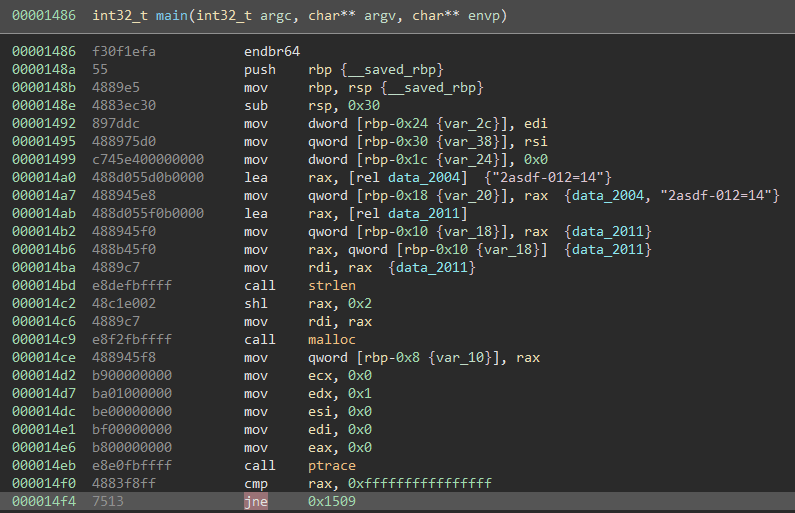
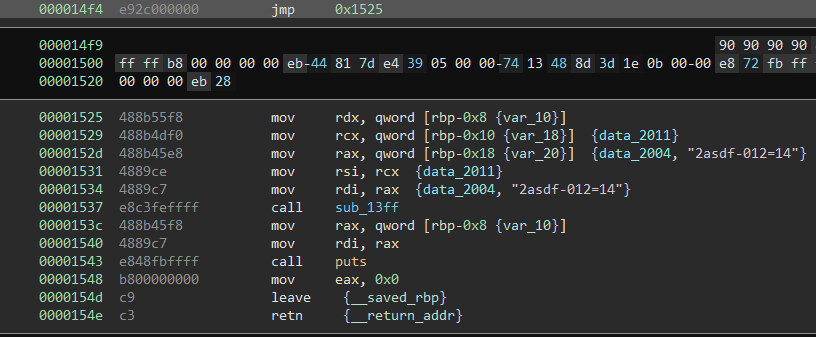
Running the patched version of this program gives us the flag.
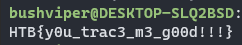
You could also do this in a debugger by setting a breakpoint before “PTRACE” is called and jumping to 0x1525, but I much prefer binary patching as I can come back and rerun it at anytime. Thanks for reading and happy reversing!

Leave a comment